you don't know whether or not your device can be jailbroken or your iPhone is able to be unlocked or not, f0recast is the tool for you. Its specially for those who are new to the jailbreaking scene. Good news is that the developer, iH8sn0w has updated f0recast to version 1.3 and it now supports the current jailbreak state.
F0recast will display the serial number of your iPhone, iPad or iPod touch, the baseband version if you're using an iPhone or 3G iPad, model number of both MC and non-MC devices and the bootloader version. It will also show whether or not your device can be jailbroken or unlocked, and which tools to use for that purpose. To use f0recast, simply connect your device to the computer and run f0recast. It will do all of the rest on its own. F0recast 1.3 is now available for both Mac and PC machines.
Download f0recast 1.3 for Windows
Download f0recast 1.3 for Mac
Tuesday, May 31, 2011
F0recast 1.3 Update Released To Check Jailbreak State Of iOS Device
Monday, May 30, 2011
How to Turn iPad 3G to Full Functional iPhone [Video]
Some Egyptian guys called iPhoneIslam Team was able to hack iPad 3G and convert it to fully functional iPhone with Cydia tweak called PhoneItiPad that will arrive to Cydia soon.

With no special hardware, all you need is jailbroken iPad 3G and your iPad 3G will do anything you expect from iPhone ... Phone Calls, SMS, FaceTime by phone number and more, thanks guys for the amazing job.
This tweak will be available via Cydia Store very soon. stay tuned
Thursday, May 26, 2011
SBSettings Offers Faster Method to Manage iPhone Settings

Then you should checkout jailbreak app - SBSettings which is a replacement of BossPrefs. Its offers faster method to manage your iPhone's settings especially if you are using some other app.
SBSettings is a jailbreak application that brings various toggle switches directly to iPhone's home screen that are available in the Settings app. SBSettings is also considered as a replacement for BossPref, which offered similar functions in iPhone firmware 1.x
SBSettings is not like the regular iPhone app that can be launched from the home screen by tapping on its icon. To launch it, you have to swipe on iPhone's status bar or tap the status bar using two fingers. Once SBSettings is launched, you'll see various toggle switches that are available in the Settings app such as Wi-Fi, 3G, EDGE, Bluetooth, Brightness etc. Just tap on the switch to disable or enable the feature (Red is "Off", Green is "On"). Isn't that a much faster method to change the settings?


Example: SBSettings Launched from iPhone Maps App






You can install SBSettings for free using Cydia on your jailbroken iPhone. As I had mentioned earlier, it does not install the application icon on iPhone's home screen like other iPhone apps. You can launch it by swiping on your iPhone's status bar or tapping the status bar using two fingers.
What do you think about SBSettings? Have you used it before? Please lets us know in the comments below.
SBSettings Toggle Allows You To Quickly Enable Or Disable Personal Hotspot Feature

Personal Hotspot was one of the most useful features introduced in iOS 4.3, which lets you connect other devices to the Internet using the iPhone 4's data connection. But it’s a pain to disable the feature when you don’t need it.
A jailbreak tweak aptly named Personal Hotspot SBSettings Toggle has recently been released that allows iPhone 4 users to quickly enable or disable the Personal Hotspot feature.
SBSettings is one of our favorite jailbreak apps as it offers a faster way to disable or enable settings like Wi-Fi, Bluetooth, 3G etc instead of the usual process of using the Settings App. Developers can also create custom toggles for SBSettings that can be installed from Cydia so that users can access them quickly from SBSettings menu.
Elias Limneos has developed the custom Personal Hotspot SBSettings Toggle, which allows you to enable or disable the Personal Hotspot feature. You can install the custom toggle for free from Cydia using these instructions:
- Install SBSettings on your jailbroken iPhone 4 if you haven’t installed it already. You checkout this post for more details.
- Launch Cydia from iPhone’s homescreen.
- Tap on the Search tab and search for Personal Hotspot SBSettings Toggle.
- Tap on Personal Hotspot SBSettings Toggle from the search results to install it on your iPhone.
You should now see the Personal Hotspot SBSettings toggle in the SBSettings menu when you swipe your finger on iPhone's status bar.

Tap on the toggle to disable (turns red) or enable (turns green) the Personal Hotspot feature.
As always, let us know if you found this toggle useful in the comments below.
Wednesday, May 25, 2011
ElcomSoft Breaks iPhone Encryption, Offers Forensic Access to File System Dumps
| May 23rd, 2011 by Vladimir Katalov |
ElcomSoft researchers were able to decrypt iPhone’s encrypted file system images made under iOS 4. While at first this may sound as a minor achievement, ElcomSoft is in fact the world’s first company to do this. It’s also worth noting that we will be releasing the product implementing this functionality for the exclusive use of law enforcement, forensic and intelligence agencies. We have a number of good reasons for doing it this way. But first, let’s have a look at perspective.
.png) Let’s make it very clear: no privacy purist should ever use an iPhone (or any other smartphone, probably). iPhone devices store or cache humungous amounts of information about how, when, and where the device has been used. The amount of sensitive information collected and stored in Apple smartphones is beyond what had previously been imaginable. Pictures, emails and text messages included deleted ones, calls placed and received are just a few things to mention. A comprehensive history of user’s locations complete with geographic coordinates and timestamps. Google maps and routes ever accessed. Web browsing history and browser cache, screen shots of applications being used, usernames, Web site passwords and the password to iPhone backups made with iTunes software, and just about everything typed on the iPhone is being cached by the device.
Let’s make it very clear: no privacy purist should ever use an iPhone (or any other smartphone, probably). iPhone devices store or cache humungous amounts of information about how, when, and where the device has been used. The amount of sensitive information collected and stored in Apple smartphones is beyond what had previously been imaginable. Pictures, emails and text messages included deleted ones, calls placed and received are just a few things to mention. A comprehensive history of user’s locations complete with geographic coordinates and timestamps. Google maps and routes ever accessed. Web browsing history and browser cache, screen shots of applications being used, usernames, Web site passwords and the password to iPhone backups made with iTunes software, and just about everything typed on the iPhone is being cached by the device.
The technique worked great until the release of iOS 4. Before that, file system images obtained from iPhone and other iOS devices were perfectly readable with all user data being readily accessible. On iOS 4.x, however, those file system images obtained from the devices were pretty much useless for forensic analysis because the contents of each file were securely encrypted. File system seemed to be intact, though, and it was still possible to get list of files and some of their attributes.
To make things even more complicated for a security researcher, every file is encrypted with its own unique encryption key tied to particular iOS device. Furthermore, certain files are protected with encryption keys tied to both the device and the user’s passcode, meaning that those files can be only decrypted when the device is unlocked by the user. Most notable examples are e-mail files maintained by built-in Mail app.
By default (with “Simple passcode” option enabled), passcodes consists of only four digits, meaning that only 10,000 possibilities exist. Having to enter their passcode pretty often most users keep their passcodes to the default length of only four digits for the sake of usability.
Ten thousand combinations do not sound like much. On a PC, breaking a passcode of this length would only take a few moments. Unfortunately, passcodes can only be bruteforced on the device itself. With iPhone 4, the maximum time of breaking a 4-digit passcode is therefore about 40 minutes, while taking about 20 minutes on average. iPhone 3GS is slower, and it takes a bit longer to break a passcode there. In fact, phones running iPhoneOS 3.x can be broken without knowing the passcode by simply removing it; with iOS 4.x, a valid passcode is required to gain full access.
It is possible to overcome the requirement of having the correct passcode by using escrow keys. Escrow keys are created and stored by the iTunes when you first plug an iOS device to the computer. Having a set of escrow keys collected from a computer to which an iOS device was once connected gives the same powers as knowing the passcode (except that you can’t deduce the passcode itself).
The last thing standing is the keychain. The keychain is a system-wide storage area for application secrets such as user account details, usernames and passwords. While Elcomsoft Phone Password Breaker already has the ability to display the contents of the keychain area, it could only read the keychain from iOS backups. As it turns out, not all data from the system keychain is exported into the backup. For example, the backup password itself is present in the system keychain but is never exported to the backup. Application developers utilizing Keychain can choose whether records stored by their application should go to the backup or not. That said, the complete Keychain including items not included wit the backup can be read and decrypted using the same set of keys obtained from the device.
The toolkit we're offering includes updated Elcomsoft Phone Password Breaker which was fitted with new function to decrypt iOS 4.x file system images, as well as an optional tools to obtain filesystem images of the iOS 4.x devices, extract keys required for image decryption, and brute-force passcode.
To make sure those tools do not fall into the wrong hands, we decided to offer them only to established law enforcement, forensic and intelligence agencies as well as select government organizations.
Next part: Extracting the File System from iPhone/iPad/iPod Touch Devices
iPhone User Data: What’s Inside
.png) Let’s make it very clear: no privacy purist should ever use an iPhone (or any other smartphone, probably). iPhone devices store or cache humungous amounts of information about how, when, and where the device has been used. The amount of sensitive information collected and stored in Apple smartphones is beyond what had previously been imaginable. Pictures, emails and text messages included deleted ones, calls placed and received are just a few things to mention. A comprehensive history of user’s locations complete with geographic coordinates and timestamps. Google maps and routes ever accessed. Web browsing history and browser cache, screen shots of applications being used, usernames, Web site passwords and the password to iPhone backups made with iTunes software, and just about everything typed on the iPhone is being cached by the device.
Let’s make it very clear: no privacy purist should ever use an iPhone (or any other smartphone, probably). iPhone devices store or cache humungous amounts of information about how, when, and where the device has been used. The amount of sensitive information collected and stored in Apple smartphones is beyond what had previously been imaginable. Pictures, emails and text messages included deleted ones, calls placed and received are just a few things to mention. A comprehensive history of user’s locations complete with geographic coordinates and timestamps. Google maps and routes ever accessed. Web browsing history and browser cache, screen shots of applications being used, usernames, Web site passwords and the password to iPhone backups made with iTunes software, and just about everything typed on the iPhone is being cached by the device.It’s Not About iPhone Backups Any More
Some, but not all, of that information makes its way into iPhone backups produced with Apple iTunes. Protected iPhone backups can be broken into with Elcomsoft Phone Password Breaker; once decrypted, information stored in these backups can be viewed by many commercial products. However, the amount of information that these backups contain is reasonably limited. Analyzing actual iPhone device could provide forensic access to much more data.Adequate Protection
The amount and nature of information accumulated by iPhone devices called for adequate protection. Starting with iPhone 3GS, Apple was including a hardware encryption chip in all subsequent devices. With iOS 4, the company introduced a feature called Data Protection that enabled hardware-based encryption of all user data stored in iPhone 3GS and subsequent models (iPhone 4, all models of iPad, and latest generations of iPod Touch). Using industry-standard AES-256 encryption, the protection was considered to be adequate against even the best equipped adversaries, including forensic analysts and law enforcement agencies.Implementation of iPhone File System Encryption
If you’re not interested in technical detail on how Apple iOS 4 protects user data in iPhone devices, you can skip this chapter. Reading it will, however, help you understand and appreciate what was done by ElcomSoft researchers. iPhone, iPod Touch and iPad (referred hereafter as iOS devices) are quite popular with all types of users. Due to their popularity and considering the amount of information about the history of user’s behavior, iOS devices are common subjects to forensic analysis. The most comprehensive technique for iOS forensics is physical acquisition that allows to obtain a bit-to-bit snapshot of iOS devices’ file system. In a way, this is similar to making an image of a disk or dumping a CD or DVD into an ISO file.The technique worked great until the release of iOS 4. Before that, file system images obtained from iPhone and other iOS devices were perfectly readable with all user data being readily accessible. On iOS 4.x, however, those file system images obtained from the devices were pretty much useless for forensic analysis because the contents of each file were securely encrypted. File system seemed to be intact, though, and it was still possible to get list of files and some of their attributes.
To make things even more complicated for a security researcher, every file is encrypted with its own unique encryption key tied to particular iOS device. Furthermore, certain files are protected with encryption keys tied to both the device and the user’s passcode, meaning that those files can be only decrypted when the device is unlocked by the user. Most notable examples are e-mail files maintained by built-in Mail app.
Breaking the Encryption
Explaining what we did to break this encryption is not exactly easy. In a word, we found a way to decrypt bit-to-bit images of iOS 4 devices. Decrypted images are perfectly usable, and can be analyzed with forensic tools such as Guidance EnCase or AccessData FTK (or any other tool which supports raw drive images and HFS+ file system). Decryption is not possible without having access to the actual device because we need to obtain the encryption keys that are stored in (or computed by) the device and are not dumped or stored during typical physical acquisition. In particular, those keys include:- Keys computed from the unique device key (UID), which is believed to be embedded in the hardware and is not extractable (so-called keys 0×835 and 0x89B);
- User passcode key which is derived from users’ passcode using the unique device key (UID);
- Escrow key(s) which are derived from escrow pairing records using the unique device key (UID);
- Effaceable storage area which stores number of encryption keys.
By default (with “Simple passcode” option enabled), passcodes consists of only four digits, meaning that only 10,000 possibilities exist. Having to enter their passcode pretty often most users keep their passcodes to the default length of only four digits for the sake of usability.
Ten thousand combinations do not sound like much. On a PC, breaking a passcode of this length would only take a few moments. Unfortunately, passcodes can only be bruteforced on the device itself. With iPhone 4, the maximum time of breaking a 4-digit passcode is therefore about 40 minutes, while taking about 20 minutes on average. iPhone 3GS is slower, and it takes a bit longer to break a passcode there. In fact, phones running iPhoneOS 3.x can be broken without knowing the passcode by simply removing it; with iOS 4.x, a valid passcode is required to gain full access.
It is possible to overcome the requirement of having the correct passcode by using escrow keys. Escrow keys are created and stored by the iTunes when you first plug an iOS device to the computer. Having a set of escrow keys collected from a computer to which an iOS device was once connected gives the same powers as knowing the passcode (except that you can’t deduce the passcode itself).
The last thing standing is the keychain. The keychain is a system-wide storage area for application secrets such as user account details, usernames and passwords. While Elcomsoft Phone Password Breaker already has the ability to display the contents of the keychain area, it could only read the keychain from iOS backups. As it turns out, not all data from the system keychain is exported into the backup. For example, the backup password itself is present in the system keychain but is never exported to the backup. Application developers utilizing Keychain can choose whether records stored by their application should go to the backup or not. That said, the complete Keychain including items not included wit the backup can be read and decrypted using the same set of keys obtained from the device.
Another World’s First
So far, ElcomSoft is the first company to offer a complete, all-in-one commercial solution for performing physical acquisition analysis of iOS 4.x devices. ElcomSoft did another “World’s first” here.What This Means for You
By breaking the protection system of Apple iPhone 3GS and later devices running iOS 4, ElcomSoft opens the possibility of an extremely comprehensive forensic analysis of affected iOS devices. While this is a big achievement in cryptographic terms, iPhone backups produced with Apple iTunes software already contained a lot of sensitive information, including keychains. ElcomSoft makes forensic analysis easier, faster (the extraction of file system encryption keys is nearly instant as opposed to lengthy dictionary or brute force attacks which are required to obtain a password to an iPhone backup) and more comprehensive.The toolkit we're offering includes updated Elcomsoft Phone Password Breaker which was fitted with new function to decrypt iOS 4.x file system images, as well as an optional tools to obtain filesystem images of the iOS 4.x devices, extract keys required for image decryption, and brute-force passcode.
To make sure those tools do not fall into the wrong hands, we decided to offer them only to established law enforcement, forensic and intelligence agencies as well as select government organizations.
Affected Apple Devices
All Apple devices starting with iPhone 3GS and running iOS 4 are affected, including iPhone, iPod and iPad devices.Next part: Extracting the File System from iPhone/iPad/iPod Touch Devices
Extracting the File System from iPhone/iPad/iPod Touch Devices | |
| May 23rd, 2011 by Andrey Belenko |
In our previous blog post we have described how we broke the encryption in iOS devices. One important thing was left out of that article for the sake of readability, and that is how we actually acquire the image of the file system of the device. Indeed, in order to decrypt the file system, we need to extract it from the device first.
 When it comes to obtaining the contents of iPhone’s file system, mobile forensic specialists usually mention the following three opportunities:
When it comes to obtaining the contents of iPhone’s file system, mobile forensic specialists usually mention the following three opportunities:
1. One can 'mount' the device, mapping it as a drive letter and copy data file after file. In this mode, I/O requests are served by the file system driver on the device that’s supposed to ‘know’ the encryption keys for all files. Essentially, this means that analyst receives file data that is already decrypted during the transfer. The ‘mounting’ in this case is achieved by using undocumented interfaces provided by Apple iTunes, which makes the researcher rely on something that’s a) undocumented, and b) involuntarily provided by the manufacturer. The amount of data available depends on whether the device is booted into a so-called "jailbroken" state or not. Devices that are not booted into a "jailbroken" state allow access to significantly less information. In "jailbroken" state, all information stored on the device may be available.
2. The second option would be to decrypt file system as a part of acquisition process so that its result is a decrypted file system.
3. Finally, one can do a physical acquisition of the encrypted file system and decrypt the data off-line. This would require an additional step of extracting required keys off the device.
The last two options are indeed very similar. In both cases, I/O requests are served by storage driver (as opposed to file system driver in the first case), effectively bypassing proprietary file system drivers and avoiding all types of file locks and access permission problems. Both methods require the device to be in "jailbroken" state.
Although those last two acquisition approaches are similar and first one might seem more attractive on the first sight, we decided to go with the last one. In our eyes, there are numerous important benefits to doing the physical acquisition in a ‘raw’ way.
1. We believe that physical acquisition should be as close to the original device data as possible. The first method (mounting the device) relies on the file system driver to deliver decrypted file data. If we wanted to implement similar on-the-fly decryption during the physical acquisition process, the resulting image won’t be a bit-to-bit physical copy at all. Instead, we can do those actions off-line, and produce a decrypted image out of a precise bit copy.
2. Some device secrets such as the passcode or escrow keys might not be known at acquisition time. Without knowing those secrets, some files can not be decrypted. Off-line processing allows capturing and storing the original encrypted image while postponing the decryption to a later moment. An analyst can return to the original image if more secrets become available (e.g. escrow keys are discovered on suspects’ desktop computer) without having to re-acquire data from the physical device.
3. Analysts may have a backlog of cases. Re-doing the acquisition with a new tool might not be what they’re looking for. With off-line approach, one can obtain the keys from the device, which takes much less time than re-imaging it.
4. Forensics often already have a favorite (or the only approved) tool to do device imaging. For those who don’t, ElcomSoft can provide a basic one that just works. As long as the tool is capable of producing raw (dd-style) images, the analysts can continue using it.
5. Finally, the tools are not bug-free. The acquisition must be as simple and as straightforward as possible. Having to re-acquire the contents of a 64 Gb iPad because of a glitch in the imaging tool could be extremely frustrating and time-consuming. By performing the decryption as a separate process, one can reduce the risk of this happening.
 When it comes to obtaining the contents of iPhone’s file system, mobile forensic specialists usually mention the following three opportunities:
When it comes to obtaining the contents of iPhone’s file system, mobile forensic specialists usually mention the following three opportunities:1. One can 'mount' the device, mapping it as a drive letter and copy data file after file. In this mode, I/O requests are served by the file system driver on the device that’s supposed to ‘know’ the encryption keys for all files. Essentially, this means that analyst receives file data that is already decrypted during the transfer. The ‘mounting’ in this case is achieved by using undocumented interfaces provided by Apple iTunes, which makes the researcher rely on something that’s a) undocumented, and b) involuntarily provided by the manufacturer. The amount of data available depends on whether the device is booted into a so-called "jailbroken" state or not. Devices that are not booted into a "jailbroken" state allow access to significantly less information. In "jailbroken" state, all information stored on the device may be available.
It is worth mentioning that booting a device into a "jailbroken" state does not necessarily require a permanent "jailbreak" modification of the device, and can be performed without modifying data stored on the device, i.e. without violating read-only principle so important in computer forensics.While relatively simple, the file-based approach has numerous limitations that make it less than ideal for forensic purposes. Since the transfer is done file-by file, the case quickly becomes difficult to manage. Typical file system contains tens of thousands of files so it might be quite a challenge to even store them in forensically sound way (i.e. making sure that no files are added, deleted, or modified after acquisition is complete). Another problem is that some files may be locked by running processes, may require additional privileges, symbolic links may interfere with the host system, etc.
2. The second option would be to decrypt file system as a part of acquisition process so that its result is a decrypted file system.
3. Finally, one can do a physical acquisition of the encrypted file system and decrypt the data off-line. This would require an additional step of extracting required keys off the device.
The last two options are indeed very similar. In both cases, I/O requests are served by storage driver (as opposed to file system driver in the first case), effectively bypassing proprietary file system drivers and avoiding all types of file locks and access permission problems. Both methods require the device to be in "jailbroken" state.
Although those last two acquisition approaches are similar and first one might seem more attractive on the first sight, we decided to go with the last one. In our eyes, there are numerous important benefits to doing the physical acquisition in a ‘raw’ way.
1. We believe that physical acquisition should be as close to the original device data as possible. The first method (mounting the device) relies on the file system driver to deliver decrypted file data. If we wanted to implement similar on-the-fly decryption during the physical acquisition process, the resulting image won’t be a bit-to-bit physical copy at all. Instead, we can do those actions off-line, and produce a decrypted image out of a precise bit copy.
2. Some device secrets such as the passcode or escrow keys might not be known at acquisition time. Without knowing those secrets, some files can not be decrypted. Off-line processing allows capturing and storing the original encrypted image while postponing the decryption to a later moment. An analyst can return to the original image if more secrets become available (e.g. escrow keys are discovered on suspects’ desktop computer) without having to re-acquire data from the physical device.
3. Analysts may have a backlog of cases. Re-doing the acquisition with a new tool might not be what they’re looking for. With off-line approach, one can obtain the keys from the device, which takes much less time than re-imaging it.
4. Forensics often already have a favorite (or the only approved) tool to do device imaging. For those who don’t, ElcomSoft can provide a basic one that just works. As long as the tool is capable of producing raw (dd-style) images, the analysts can continue using it.
5. Finally, the tools are not bug-free. The acquisition must be as simple and as straightforward as possible. Having to re-acquire the contents of a 64 Gb iPad because of a glitch in the imaging tool could be extremely frustrating and time-consuming. By performing the decryption as a separate process, one can reduce the risk of this happening.
The Toolkit
Elcomsoft Phone Password Breaker is available to general public. We will also provide eligible parties with additional acquisition Toolkit to use on devices running iOS 4.x. We’ll also provide detailed instructions. The Toolkit will allow the following:- Extract hardware-dependent keys, file system keys and escrow keys from the device;
- Recover the passcode (subject to passcode length and complexity);
- Obtain bit-to-bit copy of device storage.
Tuesday, May 24, 2011
New Windows Utility Allows You to Use AirPlay With Windows Media Center
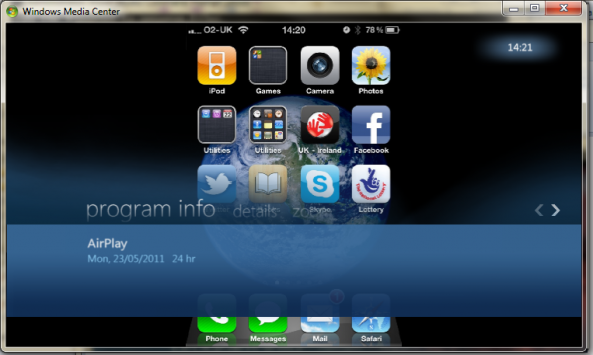
It’s becoming more and more apparent that AirPlay — Apple’s media streaming technology is here for the long haul.
We’ve seen numerous applications for both the iPhone, the Mac, and even Android devices that in some way or another, massage AirPlay’s functionality to meet their needs.
Throughout all of the fun, Windows has ultimately been left out; that is until now.
Developer Thomas Pleasance made sure of that fact with the recent release of his AirPlay enabled Windows Media Center Add-in…
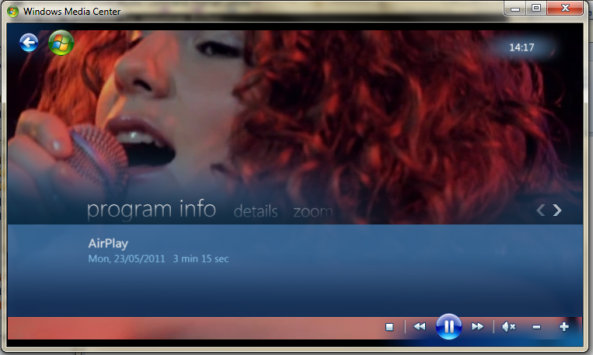
The screenshots definitely show promise, all 12 of you still running Windows Media Center in your living room should be pleased.
I tried to get this working myself, but unfortunately AirPlay doesn’t want to play nice with my Windows 7 Virtual Machine. I’m sure it would work just dandy on an actual Windows installation.
Have you tried it yet? If not, head over to Thomas’ blog and download the necessary files to get started. You will also need Bonjour installed on your machine if you have not already done so.
Thomas Pleasance
My Own Little world
AirPlay for Windows Media Center – Beta 1
Posted: May 23, 2011 | Author: Thomas Pleasance | Filed under: AirPlay, iOS, Media Center | Tags: AirPlay, Media Center | 136 Comments » I’am please to release the first beta of AirPlay For Windows Media Player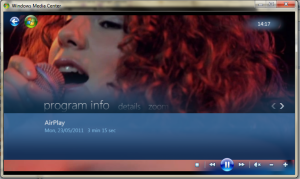
Video
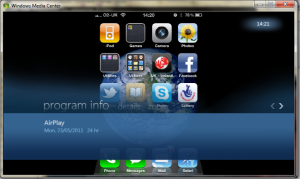
Images
Download AirPlay Client for Windows Media Center: http://goo.gl/OEzNm
Or from madeformediacenter.com
You also need Bonjour installed first: http://support.apple.com/kb/DL999
First Review: thedigitallifestyle.com
Download 4.3.3 Custom Firmware IPSW Untethered - iPhone 4, 3GS, iPad, iPod Touch 4G, 3G [Jailbreak - Activated]
Custom iOS 4.3.3 IPSW prepared with PwnageTool 4.3.3:
iPhone 4 (GSM)
- Download iPhone 4 iOS 4.3.3 Custom ipsw firmware untethered - Activated ( for users who are not on official carrier SIM card)
- Download iPhone 4 iOS 4.3.3 Custom ipsw firmware untethered - Unactivated (for users who are on official carrier SIM card)
iPhone 3GS:
- Download iPhone 3GS iOS 4.3.3 Custom ipsw firmware untethered - Activated ( for users who are not on official carrier SIM card)
- Download iPhone 3GS iOS 4.3.3 Custom ipsw firmware untethered - unactivated (for users who are on official carrier SIM card)
iPad 1 (first generation):
- Download iPad 1 iOS 4.3.3 Custom ipsw firmware untethered
iPod Touch 4G:
- Download iPod touch 4G iOS 4.3.3 Custom ipsw firmware untethered
iPod Touch 3G:
- Download iPod touch 3G iOS 4.3.3 Custom ipsw firmware untethered
- Download Apple TV 2G iOS 4.3.3 Custom ipsw firmware untethered
- Close TinyUmbrella.
- Remove Cydia's SHSH caching server from your hosts (C:\WINDOWS\system32\driver\etc\hosts)
- Reboot.
Custom iOS 4.3.3 IPSW prepared with Sn0wbreeze 2.7:
iPhone 4 (GSM)
- Download iPhone 4 iOS 4.3.3 Custom ipsw firmware untethered - Activated ( for users who are not on official carrier SIM card)
- Download iPhone 4 iOS 4.3.3 Custom ipsw firmware untethered - Unactivated (for users who are on official carrier SIM card)
iPhone 4 (CDMA) Verizon
- Download iPhone 4 iOS 4.2.8 Custom ipsw firmware untethered
- Download iPhone 3GS new bootrom iOS 4.3.3 Custom ipsw firmware untethered - Activated ( for users who are not on official carrier SIM card)
- Download iPhone 3GS new bootrom iOS 4.3.3 Custom ipsw firmware untethered - unactivated (for users who are on official carrier SIM card)
- Download iPhone 3GS new bootrom iOS 4.3.3 Custom ipsw firmware untethered -06.15 baseband Activated ( for users who are not on official carrier SIM card)
- Download iPhone 3GS new bootrom iOS 4.3.3 Custom ipsw firmware untethered -06.15 baseband unactivated (for users who are on official carrier SIM card)
iPhone 3GS Old Bootrom:
- Download iPhone 3GS old bootrom iOS 4.3.3 Custom ipsw firmware untethered - Activated ( for users who are not on official carrier SIM card)
- Download iPhone 3GS old bootrom iOS 4.3.3 Custom ipsw firmware untethered - unactivated (for users who are on official carrier SIM card)
- Download iPhone 3GS old bootrom iOS 4.3.3 Custom ipsw firmware untethered -06.15 baseband Activated ( for users who are not on official carrier SIM card)
- Download iPhone 3GS old bootrom iOS 4.3.3 Custom ipsw firmware untethered -06.15 baseband unactivated (for users who are on official carrier SIM card)
- Download iPad 1 iOS 4.3.3 Custom ipsw firmware untethered
iPod Touch 4G:
- Download iPod touch 4G iOS 4.3.3 Custom ipsw firmware untethered
iPod Touch 3G:
- Download iPod touch 3G iOS 4.3.3 Custom ipsw firmware untethered
- Download Apple TV 2G iOS 4.3.3 Custom ipsw firmware untethered
Even though Cydia doesn’t support true multitasking, with Cydia 1.1 Saurik added a new feature that allows you to resume where you last left off. The next best thing right? But, today we’re going to show you how to enable true multitasking for Cydia.
CAUTION:
1. Load Cydia and download iFile

2. Load iFile and browse to /Applications/Cydia.app
3. Locate info.plist

4. Tap on it and choose ‘Text Viewer’

5. Scroll all the way down and locate the following lines:

7. Save the file, quit iFile and restart your device
CAUTION:
- this can cause conflicts. If something goes wrong you can end up restoring your device. Use at your own risk
1. Load Cydia and download iFile

2. Load iFile and browse to /Applications/Cydia.app
3. Locate info.plist

4. Tap on it and choose ‘Text Viewer’

5. Scroll all the way down and locate the following lines:
<key> UIApplicationExitsOnSuspend </ key>6. Now tap on edit and change <true/> to <false/>
<true/>

7. Save the file, quit iFile and restart your device
[thx Valentino, via iSpazio]
HOW TO: Enable Multitasking For Cydia On iOS 4
Even though Cydia doesn’t support true multitasking, with Cydia 1.1 Saurik added a new feature that allows you to resume where you last left off. The next best thing right? But, today we’re going to show you how to enable true multitasking for Cydia.
CAUTION:
1. Load Cydia and download iFile

2. Load iFile and browse to /Applications/Cydia.app
3. Locate info.plist

4. Tap on it and choose ‘Text Viewer’

5. Scroll all the way down and locate the following lines:

7. Save the file, quit iFile and restart your device
CAUTION:
- this can cause conflicts. If something goes wrong you can end up restoring your device. Use at your own risk
1. Load Cydia and download iFile

2. Load iFile and browse to /Applications/Cydia.app
3. Locate info.plist

4. Tap on it and choose ‘Text Viewer’

5. Scroll all the way down and locate the following lines:
<key> UIApplicationExitsOnSuspend </ key>6. Now tap on edit and change <true/> to <false/>
<true/>

7. Save the file, quit iFile and restart your device
[thx Valentino, via iSpazio]
How to Get Installer - iPhone / iPod Touch / iPad - Cydia Alternative
Infini-Dev, the guys behind Installer - the world's first 3rd party app store - have successfully ported Installer to jailbroken iOS 4.3.3.
How does Installer work :
Step 1: You MUST have jailbroken iPhone, iPod or iPad, to jailbreak click
Step 2: Open Cydia > Manage > Edit > Add then add this repo "http://fr0stdev.co.cc/repo"

Step 3: Search for "Installer" and install it, congratulations, you will find Installer icon on your Springboard

Yesterday we had succeed "porting" Installer to 4.3.3 and below.
Installer was worlds first 3rd party app store, Introduced by NullRiver, or later known as RipDev.
RipDev was awesome at Installers, they also made Icy, Hood, and other apps.
Icy is also ported by us, and released 1 month ago.
How does Installer work :
Installer works with a different system than Cydia, that wy you won't be able to add a Cydia repo into installer.How to install Installer on iPhone, iPod touch or iPad :
As we speak we are working on a new community source for installer only, wich means you will be able to install things via installer.
We could use help, you may help us by submitting apps that where hosted by installer, or apps that have the installer structure. Or by making app with a installer structure.
Right now, Installer claims to work on every single iOS released after 2.1, even on 4.3.3
Step 1: You MUST have jailbroken iPhone, iPod or iPad, to jailbreak click
Step 2: Open Cydia > Manage > Edit > Add then add this repo "http://fr0stdev.co.cc/repo"

Step 3: Search for "Installer" and install it, congratulations, you will find Installer icon on your Springboard

Tuesday, May 17, 2011
Wireless router Powerful 3G or DSL functions to Wifi enable
1. Supports GRPS/EDGE,cdma2000 EVDO Rev.A, WCDMA HSDPA/HSUPA, TD-WCDMA HSPA protocol, widely supports 3G/3.5G/3.75G USB modems.
2. Supports auto dialup when power on, supports Auto APN function which can indentify your 3G modem intelligently and start to dialup , truly plug and play.
3. Supports fixed time dialing, many options can be choosen, such as a special time range, for instance, from 9:00 AM to 18:00 PM, or from Monday to Friday and so on.
4. Supports 3G online time statistics, by this feature, you can easily know total online time that spent on 3G at any time.
5. With one 3G Router, one 3G Modem, it's most affordable way to share connectivity with computers, mobile phone, wifi enabled devices anywhere, whether in the office, at home, in the dormitory, in the factory, you can experience 3G low delay, high speed, high stability applications in the 3G signal coverage areas
Main functions
1. Supports 3G, PPPoE, static IP, dynamic IP(DHCP) broadband functions.
2. Wireless security 2 with 64bit/128-bit WEP, and WPA-PSK/WPA2-PSK support.
3. Built-in SPI firewall, supports IP filtering, MAC filtering, Domain filtering.
4. Block DDOS attacks from LAN support.
5. Supports remote access control for web base access, remote Telnet.
6. Supports Virtual Server, UPnP, Special Application, DMZ host ideal for creating a personal website within your LAN.
7. WDS repeater function support.
8. Built-in DHCP server with automatic dynamic IP address distribution.
9. Friendly user interface, supports free web software updates




2. Supports auto dialup when power on, supports Auto APN function which can indentify your 3G modem intelligently and start to dialup , truly plug and play.
3. Supports fixed time dialing, many options can be choosen, such as a special time range, for instance, from 9:00 AM to 18:00 PM, or from Monday to Friday and so on.
4. Supports 3G online time statistics, by this feature, you can easily know total online time that spent on 3G at any time.
5. With one 3G Router, one 3G Modem, it's most affordable way to share connectivity with computers, mobile phone, wifi enabled devices anywhere, whether in the office, at home, in the dormitory, in the factory, you can experience 3G low delay, high speed, high stability applications in the 3G signal coverage areas
Main functions
1. Supports 3G, PPPoE, static IP, dynamic IP(DHCP) broadband functions.
2. Wireless security 2 with 64bit/128-bit WEP, and WPA-PSK/WPA2-PSK support.
3. Built-in SPI firewall, supports IP filtering, MAC filtering, Domain filtering.
4. Block DDOS attacks from LAN support.
5. Supports remote access control for web base access, remote Telnet.
6. Supports Virtual Server, UPnP, Special Application, DMZ host ideal for creating a personal website within your LAN.
7. WDS repeater function support.
8. Built-in DHCP server with automatic dynamic IP address distribution.
9. Friendly user interface, supports free web software updates







Subscribe to:
Comments (Atom)
Posted Threads
-
▼
2011
(503)
-
▼
May
(34)
- F0recast 1.3 Update Released To Check Jailbreak St...
- How to Turn iPad 3G to Full Functional iPhone [Video]
- SBSettings Offers Faster Method to Manage iPhone S...
- ElcomSoft Breaks iPhone Encryption, Offers Forensi...
- New Windows Utility Allows You to Use AirPlay With...
- Download 4.3.3 Custom Firmware IPSW Untethered - i...
- Even though Cydia doesn’t support true multitaskin...
- HOW TO: Enable Multitasking For Cydia On iOS 4
- How to Get Installer - iPhone / iPod Touch / iPad ...
- Make a single access point to internet via 3G or D...
- Wireless router Powerful 3G or DSL functions to Wi...
- Resn0w 0.9.6rc16: Fix Side Switch and Vibration Pr...
- How to Save 4.3.3 / 4.2.8 SHSH iPhone, iPod Touch,...
- Apple Releases iOS 4.2.2 for Apple TV
- Save SHSH of iOS 4.3.3 and 4.2.8 Using iSHSHit 1.0.8
- Apple Releases iOS 4.2.2 for Apple TV
- The Best Windows 7 Tablets at CES 2011
- Top 20 best tablet PC iPad alternatives
- Sn0wbreeze Updated To v2.7.1 To Fix Vibration Issue
- How to Save 4.3.3 / 4.2.8 SHSH iPhone, iPod Touch,...
- How to Jailbreak iOS 4.3.3 iPhone 4, 3GS, iPod Tou...
- No title
- Cydia™ Search Online using your Desktop
- Redsn0w 0.9.6 RC15 untethered jailbreak for iOS 4.3.3
- Ultrasn0w 1.2.3: to unlock 4.3.3 iPhone 4 3GS
- 4.3.3 iOS Jailbreak iPhone 4, 3GS, iPod Touch 4G, ...
- How to Use Sn0wbreeze To Untethered Jailbreak iOS ...
- Jailbreak 4.3.3 iPhone 4, 3GS, iPod Touch 4G, 3G, ...
- iMac Hands-on Video
- Apple Releases iOS 4.3.3 [Direct Links]
- Sn0wbreeze Updated To v2.6.1 To Untethered Jailbre...
- ipswDownloader Changed to openIPSW - iOS Firmware ...
- How to Install Icy (Cydia Alternative) on iPhone 4...
- Lima: New Browser Based Jailbreak App Installer To...
-
▼
May
(34)












